Hiding in plain sight: Requirements for avoiding the Snoopers Charter in the UK
Preface: #
Snoopers Charter is the colloquial name we use to refer to the Investigatory Powers Act in the United Kingdom. If you’ve been living under a rock this past couple of years you can read a very detailed description of it here. tl;dr It forces ISPs to keep records of your internet history and gives the government the right to read that data; it is the first of it’s kind in a western country and has unfortunately been summarily repeated in countries such as The Netherlands
Amber Rudd seems to be highly in favour of it but she’s not known for being tech savvy and she’s not a known supporter of free speech.. But I digress.
This Article is not about the investigatory powers act itself, this is meant to provide my slightly less technical friends with some advice about how to go about being a bit more private in that kind of hostile climate, and to talk about the sliding road we’re going to do down a little.
If you want to get to the meat of the article click here
Slippery Slope #
Now that we know the government is forcing ISPs and cell carriers to log our communications (PS: this includes anything they can get their hands on, search histories, messages to friends/partners, business information) we can speculate what will happen next.
“But that’s speculation and it won’t happen”
Honestly all those things I listed above are actually not affected yet, Amber Rudd can’t get a lot of that information because it’s protected with TLS/SSL.
TLS/SSL is the way we make sure that nobody can listen in on your communication with websites, it’s what makes your online banking safe from people sitting on your wifi.
But Amber Rudd and co. are already making waves about breaking this encryption, which is why I believe we will see the right to keep things secure removed in a short space of time.
If you have a techy friend then you’ve probably heard them talk about something called a VPN, which will keep you safe from prying eyes.
VPNs work by making an encrypted connection between your computer to someone elses server, which will then allow you to access the internet as if you’re computer was situated where the server is.
This is great for things like Netflix where you want to “be” in the USA, or on wifi that you don’t trust, but you want to do something that doesn’t use SSL/TLS (as I mentioned above).
However, VPNs aren’t perfect. If they’re implemented improperly they leak DNS requests.
DNS is the mechanism that allows domains/websites to be translated into something your computer understands, if you see someones DNS queries you can tell what sites they’re trying to visit, even if the connection is encrypted. This is what we in the industry would call “metadata”.
Even if you find a perfect VPN however, if the government notices an uptick in VPN traffic it will very likely try to demonise those who use VPNs.
They may even force ISPs to send letters to those who use VPNs a lot. I imagine they will use “terrorists” or “save the children” tactics here too.
“Only pedophiles use VPNS!”
and
“Latest terrorist tragedy could have been prevented, but the guy who randomly drove a van into a crowd of people without talking to anyone had VPN software on his laptop!”
So, if you see that kind of headline in future, just know that they’re doing that because they want control over your discourse online, they want you to know that you’re monitored to ensure you don’t speak to your friends too openly about your disdain for certain policies.
“You’re ranting Jan, tell me what it means” #
If/when VPNs are discredited there will be startlingly few ways to protect yourself. It is quite likely that they will already flag a VPN user and apply a little more introspection on that person as a result. “We have reason to believe you’re hiding something”. So, for this reason it is fundamentally important to be able to hide in plain sight.
The Meat #
DNS #
I mentioned above that DNS data is essentially metadata. That means you’re giving away information about what site you want to visit to anybody listening, unencrypted.
This kind of metadata doesn’t have to be given up at all, you can install something called DNSCrypt which will encrypt your DNS queries. Job done!
…. Except for HTTPS issues …
HTTPS #
I mentioned HTTPS/TLS/SSL above, this is how you generally connect to websites, it happens over “port 443”. Historically SSL meant you could only server one site on one server. Since the IPv4 address space started getting congested (please also ask your ISP for IPv6!) we needed a way to address multiple sites on the same server. To that end something called “SNI” came in, which stands for “Server Name Identification”. This basically exposes the site you’re visiting to someone listening in, because it’s sent to the server unencrypted. Eg:
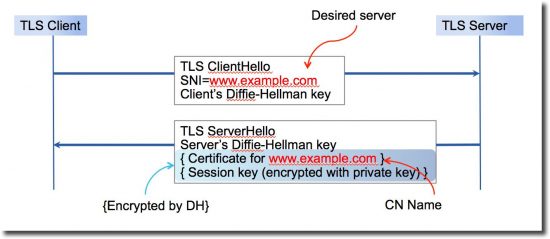
As you can see, the metadata about the site you want to reach is still exposed. Even if you had used a service such as DNSCrypt it would still be possible to know what site you wanted to go to.
What is not possible however, is to know what you were doing on the site, what pages you visited there and things like your username.
So this is a step in the right direction at least.
Anyconnect/OpenConnect #
This should be tacked on to HTTPS, but I feel it needs it’s own section.
Anyconnect is a Cisco (networking company) based VPN software for big companies.
OpenConnect and ocserv is the open source (and free.. for you!) version of the same software.
Why this over anything else?
Well, in order to do VPNs in random corporate offices you need to bypass HTTP proxies.. A lot of companies will disconnect you from the outside world and force you to go through special machines which only let out HTTP/HTTPS traffic.. So Cisco invented a way to do VPNs over HTTPS.
This is great for us, since now we have the ability to look like we’re just talking to one “site” which would be our VPN server.
Effectively to our ISP (BT/Virgin/Whomever) we look like an ordinary internet user!
“But Jan, I don’t know how to find such a server”
There is a project called Streisand which would allow you to make a very quick and easy VPN server very rapidly.
If I get enough requests I’ll build a small platform for bringing up and tearing down instances.
please note: if the Conservative government in the United Kingdom successfully outlaw end-to-end encryption.. VPNs will be illegal.
This article only informs you of what to do when they start going after people who use VPNs.